Social Engineering is the art of manipulating, influencing, or deceiving you in order to gain control over your computer system. The hacker might use the phone, email, snail mail or direct contact to gain illegal access. Phishing, spear-phishing, and CEO Fraud are all examples.
How dangerous is social engineering?
“…Many of the most damaging security penetrations are, and will continue to be, due to Social Engineering, not electronic hacking or cracking… Social Engineering is the single greatest security risk in the decade ahead.” — Gartner, 2010
Social Engineer
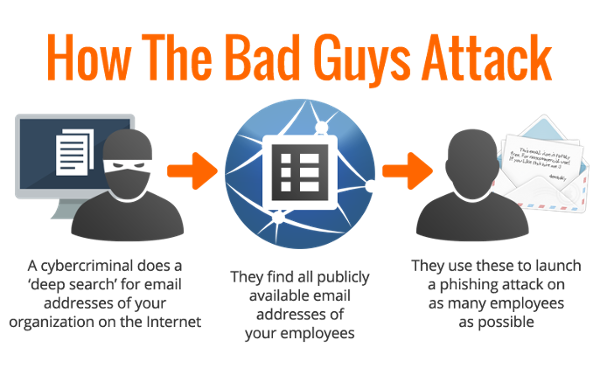
OK, so who are these people? It could be a hacker in the USA who is out to do damage or disrupt. It could be a member of an Eastern Europe cybercrime mafia that is trying to penetrate your network and steal cash from your online bank account. Or, it could be a Chinese hacker that is trying to get in your organization’s network for corporate espionage.
Techniques
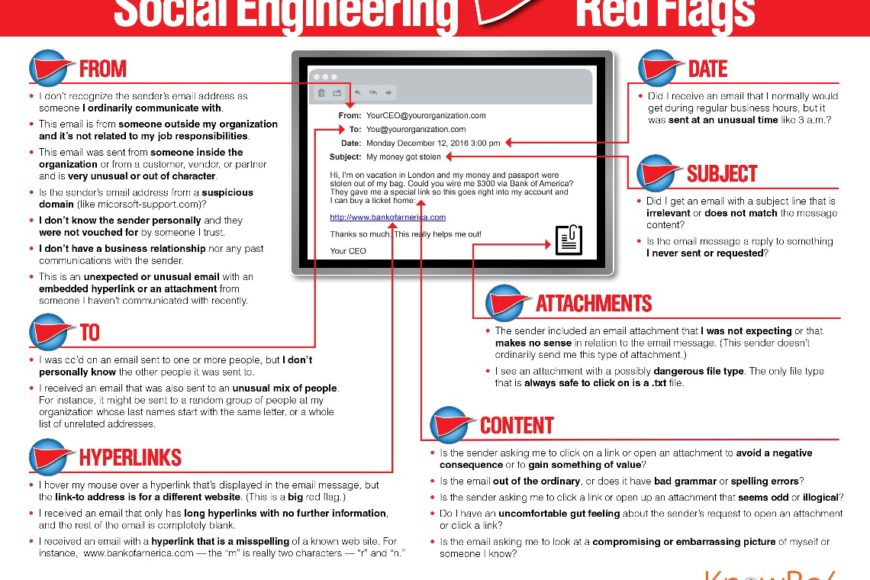
What does this tactic look like in action? It could look like an email that has been designed to seem like it is from a credible organization, like the Better Business Bureau. But if you open it and click on that attachment, you could be installing malware. Or, it could be disguised to look like it comes from someone inside your organization – someone whom you trust. But if you respond to that email with your user name and password, your computer is easily compromised. The rule is Think Before You Click.
Examples
Cybercriminals create bogus profiles on social media and try to trick you. They will impersonate a celebrity or one of your friends or colleagues. These profiles look very much like the real thing, and it’s easy to get tricked. They try to impersonate a celebrity that the bad guys already know you like a lot.
Let’s say you were tricked into believing a bogus Social Network profile. The next step is that they try to make you click on a link or install malicious software, often something to watch a video. If you click, or do that install, it’s highly likely you will infect your desktop with malware that allows the attacker to take over your PC.
Attacks
You may have heard of Norton antivirus, published by Symantec. The technical director of Symantec Security Response said that bad guys are generally not trying to exploit technical vulnerabilities in Windows. They are going after you instead. “You don’t need as many technical skills to find one person who might be willing, in a moment of weakness, to open up an attachment that contains malicious content.” Only about 3% of the malware they run into tries to exploit a technical flaw. The other 97% is trying to trick a user through some type of social engineering scheme. This means it does not matter if your workstation is a PC or a Mac. The final line of defense is… you guessed it: YOU !